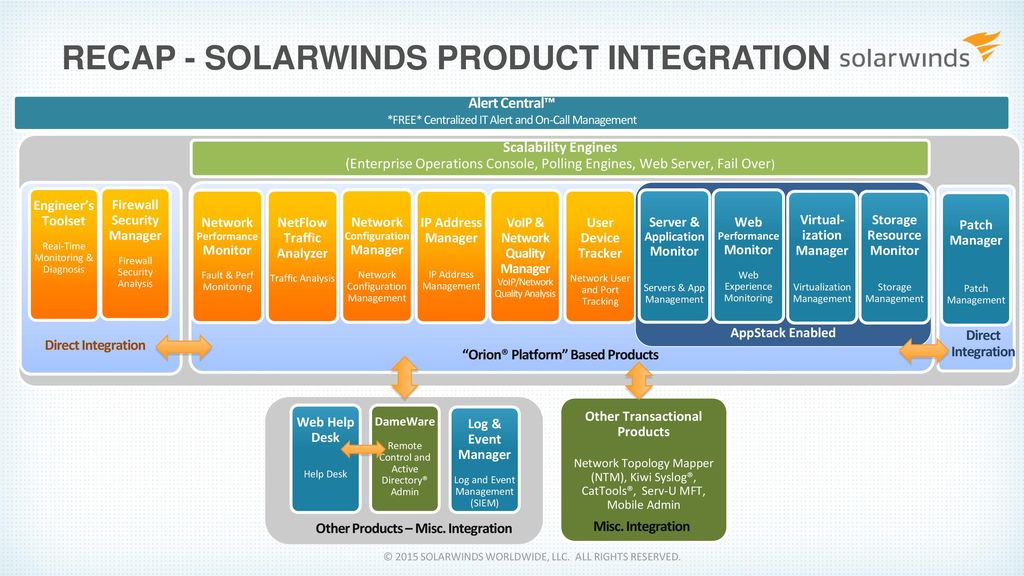
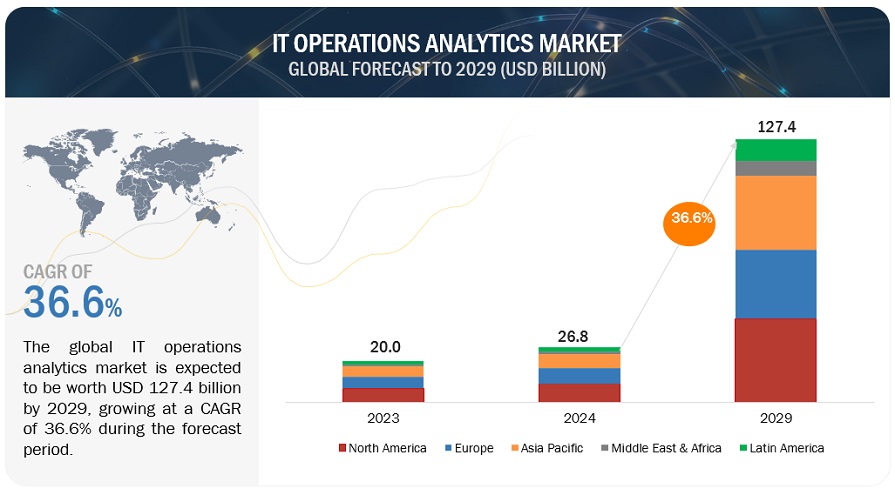
Solarwinds Firewall Security Manager 6 6 5
Solarwinds firewall security manager 6 6 5 client session handling metasploit.
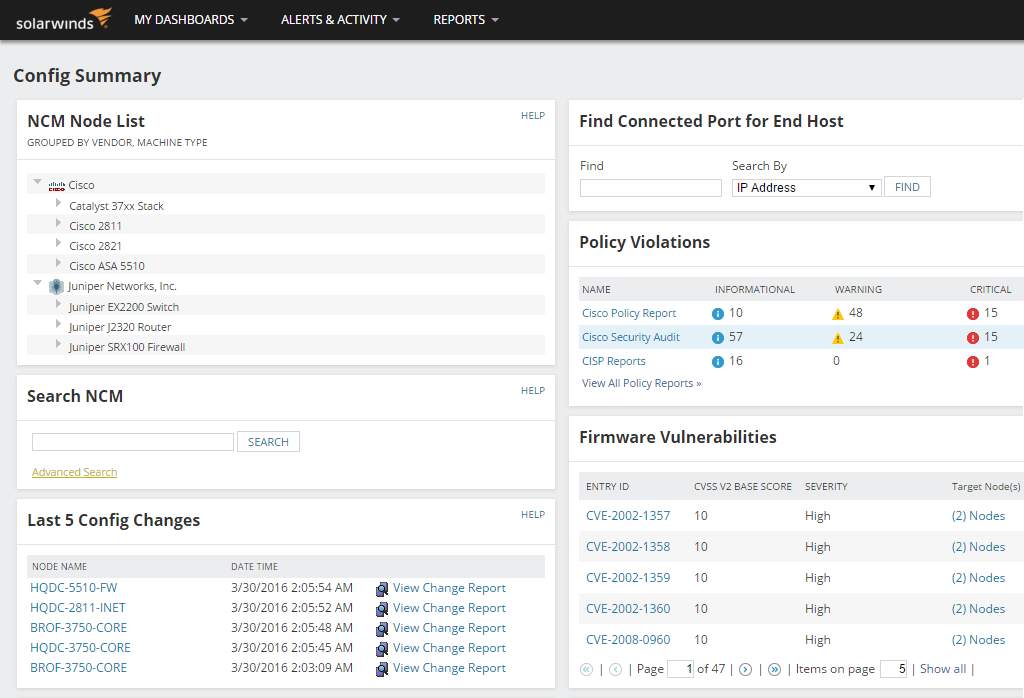
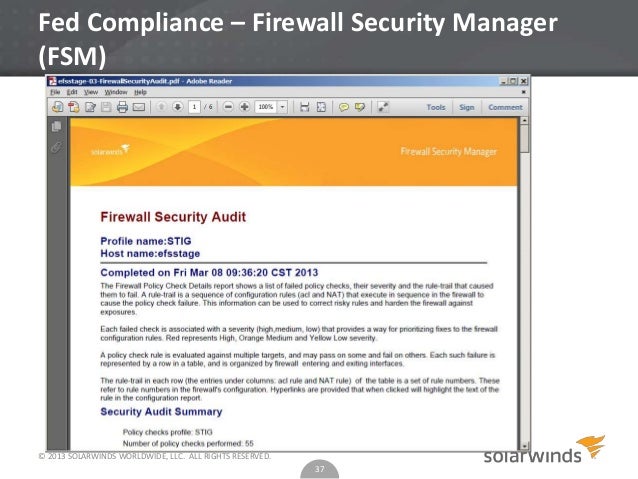
Solarwinds firewall security manager 6 6 5. Real user and synthetic monitoring of web applications from outside the firewall. Remote exploit for windows platform. This allows it teams to more quickly identify anomalous activities like when a connection is denied by firewall rules or intrusion activity like port scans. To determine the complete firewall security audit trail you can choose a time window run a specific report then use the select expert utility.
The first vulnerability is an authentication bypass via the change advisor interface due to a. Note about upgrade to fsm 6 5. Download solarwinds firewall security manager 6 6 from our software library for free. The most popular version among the software users is 6 5.
The release notes referenced above contain important information about upgrades from your current version of firepac or fsm to fsm v6 5 we recommend that users spend a few minutes reviewing them especially if you plan to perform an upgrade from firepac deployed in standalone mode to fsm v6 5. With solarwinds security event manager sem users can leverage continuous monitoring capabilities to keep track of firewall activity. This module exploits multiple vulnerabilities found in solarwinds firewall security manager 6 6 5. Virus free and 100 clean download.
The first vulnerability is an authentication bypass via the change advisor interface due to a user controlled session putvalue api in userlogin jsp allowing the attacker to set the username attribute before authentication. Also the software is known as solarwinds fsm server. This metasploit module exploits multiple vulnerabilities found in solarwinds firewall security manager 6 6 5. Name solarwinds firewall security manager 6 6 5 client session handling vulnerability description q this module exploits multiple vulnerabilities found in solarwinds firewall security manager.
Security event manager s firewall auditing tool includes over 300 built in audit report templates for standards such as pci dss sox hipaa disa stig and these are available from the reports console. The current installer available for download occupies 237 5 mb on disk. The first vulnerability is an authentication bypass via the change advisor interface. Monitoring and visualization of machine data from applications and infrastructure inside the firewall extending the solarwinds orion platform.